iPhone Vulnerability Makes It Easy to Access Your Pin Protected Data

The vulnerability was discovered by Bernd Marienfeldt and applies to various firmware versions.
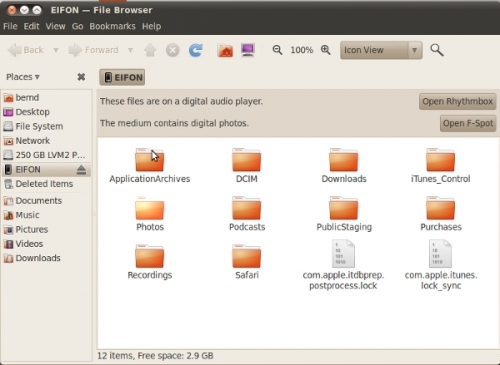
The contents sample have been collected off a non jail broken iPhone 3GS (with latest iPhone OS installed, all apps fully up to date and immediately PIN lock enabled) by simply connecting it powered off via USB to a Linux Lucid Lynx PC (10.04) and then switched back on – being automatically mounted with given insecurity and never been attached to the PC before.
Merienfeldt believes the allowed write access could also lead into triggering a buffer overflow. Apple thinks they understand why this can happen but cannot provide timing or further details on the release of a fix.
Read More [via Robert]Related posts:
- iPhone Password Breaker: Recover Password-Protected iPhone And iPod Backups
- How to Disable Edge/3G Data on Your iPhone
- JuicePhone: Extract Data From iPhone Backups
- How to Access More Than 180 Apps or WebClips via Spotlight on iPhone 3.0
Related posts brought to you by Yet Another Related Posts Plugin.